When KYT tools turn into "zombie systems": The compliance you think you have may actually be a trap
Anyone in the industry knows there are two kinds of compliance: the kind you show to regulators, and the kind that actually works. The former is known as “Compliance Theater”—a show put on for appearances—while the latter is true, substantive risk management. The sad reality is that most organizations, especially fast-moving fintech companies, are unknowingly stuck performing the former.
So what really is “Compliance Theater”? It’s a carefully orchestrated performance designed to pass inspections, secure licenses, and reassure investors. On this stage, following procedures perfectly is everything, and slick reporting trumps real risk identification. The actors—compliance officers—recite prepared scripts (compliance manuals), manipulating flashy props (expensive systems), all to convince the audience (regulators) that all is well. As long as the show looks good, licenses are granted, capital flows in—everyone’s happy.
The most dazzling, costly, and deceptive props are the so-called “zombie systems”—platforms that seem to run 24/7 but, in truth, have lost all effectiveness. This includes KYT (Know Your Transaction) systems, intended to be the front line of anti-money laundering (AML), which often become the first casualties—turning into budget-sucking zombies that provide false peace of mind. They lay dormant on the server, green lights blinking, reports generated—everything “normal”—until a real crisis explodes right under their nose.
This is compliance’s greatest trap. You may think you’ve bought the best gear and built an ironclad defense, but really, you’re just pouring money and resources into a zombie. It won’t protect you—when disaster strikes, you’ll be left clueless about what went wrong.
This begs the question: Why do KYT tools procured at great cost and effort sometimes degenerate into useless shells? Is it a fatal technical mistake, a process management meltdown, or a combination of both?
Today, let’s turn our focus to the fintech and payments industry—the main stage of “Compliance Theater”—with special attention to the fast-growing, complex Southeast Asian market, where real dramas are unfolding. Our job: pull back the curtain and see what’s really happening backstage.
Act One: Dissecting Zombie Systems—How KYT Tools “Die”
A zombie system doesn’t collapse overnight. It doesn’t fail from one massive bug or a catastrophic crash—instead, it gradually loses its ability to sense, analyze, and respond while appearing to operate “normally” day after day. Eventually, it’s just a hollow shell keeping the lights on. We can break this down from a technical and a process standpoint to see how even the best KYT system can waste away into a zombie.
Technical “Brain Death”: Single Points of Failure and Data Silos
Technology is the brain of a KYT system. When its neural connections are cut, when data stops flowing, when analytic models harden, the system enters “brain death.” It might keep processing data, but understanding and judgement are lost.
The Blind Spots of a Single Tool: Seeing the World with One Eye
Overreliance on a single KYT tool is the most common and damaging cause of system failure. Insiders know this, but in the “Compliance Theater” script, it’s often ignored for the sake of “authority” or “streamlined management.”
Why is one tool a fatal flaw? Because no single tool can catch everything. It’s like asking a guard to watch every direction—there will always be blind spots. A MetaComp study from a licensed Singapore digital asset service provider analyzed over 7,000 live transactions and found that depending on only one or two KYT tools meant as much as 25% of high-risk transactions passed through undetected. That’s ignoring a quarter of your risk—not just a blind spot, but a black hole.
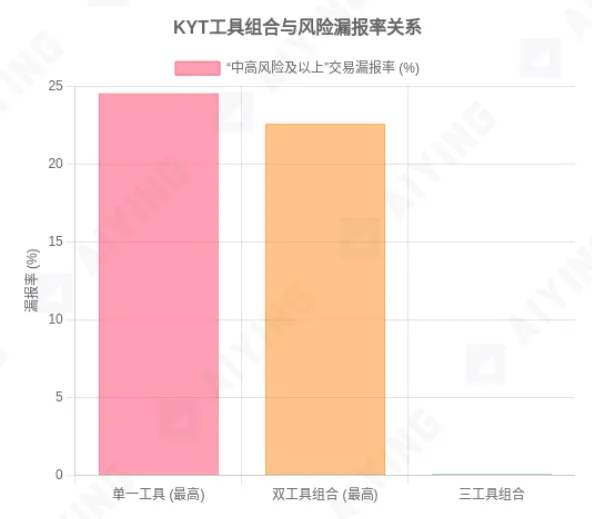
Figure 1: Comparison of False Clean Rates for Different KYT Tool Combinations
Source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. Data shows that when the risk threshold is set to “medium-high,” a single tool has a false clean rate of up to 24.55%; two tools, up to 22.60%; with three tools, it drops to just 0.10%.
This exposure is driven by inherent flaws in the KYT tool ecosystem. Every tool is built on its own datasets and intelligence models, leading to persistent differences and blind spots, such as:
- Data source differences: Some tools have better visibility over North American risk addresses due to ties with US law enforcement; others are stronger in Asia, with better local fraud intel. No single tool covers every geography equally well.
- Different risk specialties: Some tools excel at OFAC list tracking, others are built to detect mixers or darknet addresses. If your tool can’t spot your primary risks, it’s basically for show.
- Sluggish updates: Black market addresses are fleeting. A risk address tagged by one tool today might not get picked up by another for days or weeks—plenty of time for money launderers to act.
So when you rely on just one KYT tool, you are gambling—that all the threats you face will just happen to be in its field of vision.
Data Silos and “Malnutrition”: A River Without a Source Cannot Flow
Single-tool blindness is bad enough, but data silos cause outright malnutrition. KYT systems don’t operate in a vacuum; effectiveness depends on a holistic view of counterparties and behavior, requiring steady data feeds from KYC, risk rating, and business systems. When those pipelines are blocked or low quality, the KYT system is running dry.
This is common in fast-growing payment companies:
The KYC team’s onboarding data is siloed in System A. The risk team’s transaction monitoring runs in System B. The compliance team files AML reports in System C. Each system is from a separate vendor and department—no real-time data sharing. The KYT system, when analyzing a live transaction, may depend on a static risk profile from KYC set three months prior. If the customer’s risk behaviors have changed, but that data is stuck in the risk team’s system, the KYT system is working blind.
The direct consequence: the KYT system can’t build an accurate behavioral baseline for each customer. A core function of KYT is to spot “anomalies”—deviations from the norm. But if it doesn’t know what “normal” is, how can it spot “abnormal”? It falls back on the crudest static rules, flooding teams with useless alerts and creeping ever closer to zombie status.
Static Rules: Searching for New Lands with an Old Map
Criminal methods evolve constantly—from old-school “smurfing,” to laundering through DeFi protocols and NFT wash trades. The complexity and concealment are rising fast. Yet many “zombie KYT systems” are stuck with rulebooks from years ago; they’re looking for new continents with outdated maps, and they’re doomed to fail.
Static rules—like “flag any transaction over $10,000”—are trivial for criminals to evade. They simply use automation to split large amounts into hundreds or thousands of smaller payments. The real threats lurk in complex behavioral patterns, such as:
- A new account makes lots of small, frequent payments to unrelated parties.
- Funds flow in and are instantly broken up and sent to multiple addresses—a classic “peel chain.”
- Transactions touch high-risk mixers, unregistered exchanges, or sanctioned jurisdictions.
Static rules can’t capture these. You need machine learning models that learn from transaction networks and massive data sets. A healthy KYT system should have continuously evolving rules and models. A zombie system stops updating, and quickly falls hopelessly behind.
Process “Cardiac Arrest”: From “Set and Forget” to “Alert Fatigue”
Technical failure causes “brain death,” but process failure causes “cardiac arrest.” Even the best tech is worthless without the right processes to drive it. In “Compliance Theater,” process failure is often subtler and more destructive than tech failure.
The “Live Means Victory” Illusion: Mistaking the Wedding as the End of the Story
Many companies—especially startups—see compliance as a project. They view the purchase and rollout of a KYT system as a finite job. Once live and regulatory signoff is achieved, “victory” is declared. This confusion—treating the wedding as the end of love—is classic “Compliance Theater.”
Going live is just day one of a KYT system. It’s not a “set and forget” tool, but a living system needing constant maintenance and improvement:
- Continuous parameter tuning: Markets and behaviors change, so must thresholds and risk settings. Last year’s $10,000 trigger may be useless as volumes rise.
- Ongoing rule improvements: New risks require new rules; old rules that generate only false positives need to be retired.
- Regular ML retraining: Model decay is real—use fresh data to keep machine learning accurate against new risks.
If no one is responsible, if there’s no budget, the KYT system becomes a neglected sports car—rusting away in the garage until it’s scrap.
“Alert Fatigue”—The Last Straw for Compliance Teams
A badly configured, neglected zombie system’s most direct—and disastrous—consequence is a flood of false alarms. In many financial institutions, over 95%, sometimes even 99% of KYT alerts are false positives. That’s not just inefficient—it leads to “alert fatigue.”
Imagine a compliance officer’s daily grind:
Each morning brings hundreds of new alerts. He investigates the first one for half an hour—normal business, closes it. Second one, same. Third one, ditto. Day after day, he’s drowning in false alarms. Initial diligence becomes numbness. He looks for shortcuts, stops trusting the system, and when a truly high-risk alert arrives, he might dismiss it with barely a glance.
Alert fatigue destroys compliance. It turns teams from risk hunters into mere cleaners, sapping morale and letting criminals slip through under the noise.
At that stage, the KYT system’s “heartbeat” is meaningless—nobody responds or trusts it. It’s a zombie.
A friend’s company once pursued a license and investor approval in classic “Compliance Theater”—loudly touting a top-tier KYT tool as proof of “highest compliance standards,” but bought only one vendor’s system to save money. Their thinking: “We used the best—don’t blame us if something happens.” They forgot even the best tool has blind spots.
The compliance team was understaffed and not tech-savvy, so they used only the vendor’s basic static rules—monitoring big transactions and a few blacklist addresses, calling it done.
As soon as transaction volume spiked, the system was buried in alerts. Junior analysts found 95%+ were false positives. To hit their KPIs, they shifted from risk reviews to “close alerts” mode. Soon, no one cared about the alerts at all.
Money laundering professionals quickly took advantage. Using classic “smurfing,” they broke illegal gambling proceeds into thousands of tiny transactions—below the monitoring threshold—posing as e-commerce refunds. It wasn’t the KYT system that finally raised the alarm, but their partner bank. When regulators’ inquiry letters landed on the CEO’s desk, he was at a loss. Reportedly, the company later lost its license.
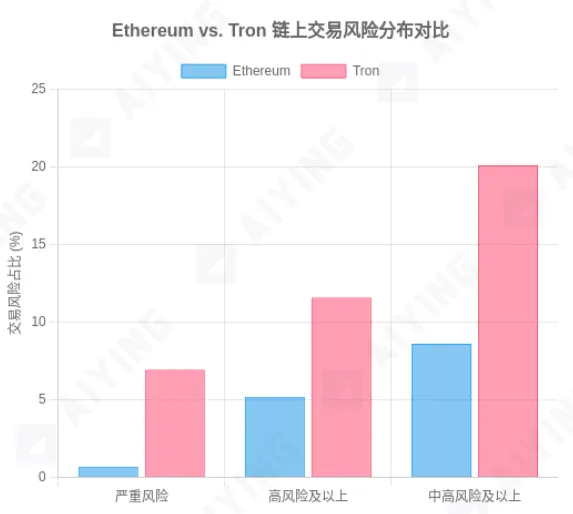
Figure 2: Blockchain Network Risk Level Comparison
Source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. In the sample, Tron chain transactions were labeled “severe,” “high,” or “medium-high” risk at a significantly higher rate than Ethereum chain.
Stories like this are a mirror for countless fintechs stuck in “Compliance Theater.” Many are still standing only because they’ve been lucky so far and haven’t been targeted by criminals. That luck won’t last forever.
Act Two: From Zombie to Sentry—How to Awaken Compliance
Having exposed the disease of zombie systems and the tragedy of “Compliance Theater,” we can’t stop at criticism. On the front lines, what matters is: How do we fix it? How do we revive a dying zombie into a battle-ready sentry?
The answer isn’t buying a more expensive “authoritative” tool, but driving a change in mindset and tactics across the board. This approach is old news to hands-on professionals, but MetaComp’s research is the first to quantify and publish it as an executable playbook.
Core Solution: Stop the Solo Act—Build Layered Defense
First, throw out the “buy a tool and you’re done” idea. Real compliance isn’t a solo act—it’s a trench war requiring a layered defense. One sentry can’t stop a whole army; you need sentries, patrols, radar, and intelligence—an integrated network.
Tactical Core: The Multi-Tool Combo
The heart of this defense is the multi-tool combo. One tool’s blind spots are inevitable, but several can cover for each other. Cross-validation narrows down hiding places for risk.
How many tools do you need? Two? Four? More?
MetaComp’s research answers: the “three-tool combo” is the sweet spot for balancing effectiveness, cost, and speed.
Think of it this way:
- Tool 1: Your sentry—broad coverage, catching most routine risks.
- Tool 2: Your patrol—specialized knowledge (e.g., DeFi risk or regional insight) for threats the sentry misses.
- Tool 3: Your back-end analyst—strong data correlation, tying loose ends into a full risk picture.
The synergy of three tools is exponential. Data shows that adding a third tool cuts the false clean rate for high-risk transactions to under 0.10%—catching 99.9% of known threats. That’s true, effective compliance.
Adding more tools brings diminishing returns and can slow you down: four tools may take 11 seconds per check, while three hold it to about two seconds. In real-time payments, that extra lag could mean lost customers.
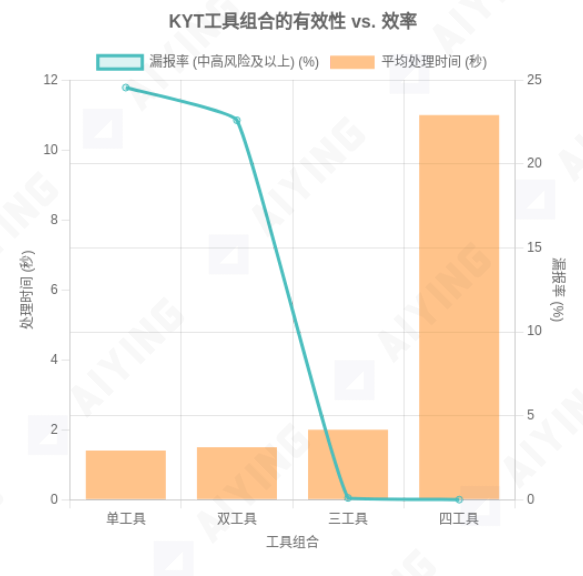
Figure 3: Tradeoffs in Effectiveness and Speed Using Different KYT Tool Combos
Source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. The chart illustrates that while more tools reduce false clean rates, they increase processing time; three tools offer the optimal balance.
Turning Methodology into Action: Build Your Own Rule Engine
Choosing your “trio” is just an upgrade in hardware. The key is integrating them in one command center—a rule engine independent of any single vendor.
Step 1: Standardize Risk Categories—Speak the Same Language
Don’t let the tools dictate how you think. Different tools tag the same risks with different labels—“Coin Mixer,” “Protocol Privacy,” “Shield,” etc. Your compliance staff shouldn’t have to memorize each tool’s dialect. Build a standardized risk classification and map all risk tags from any tool to your system.
For example, set internal risk categories as follows:
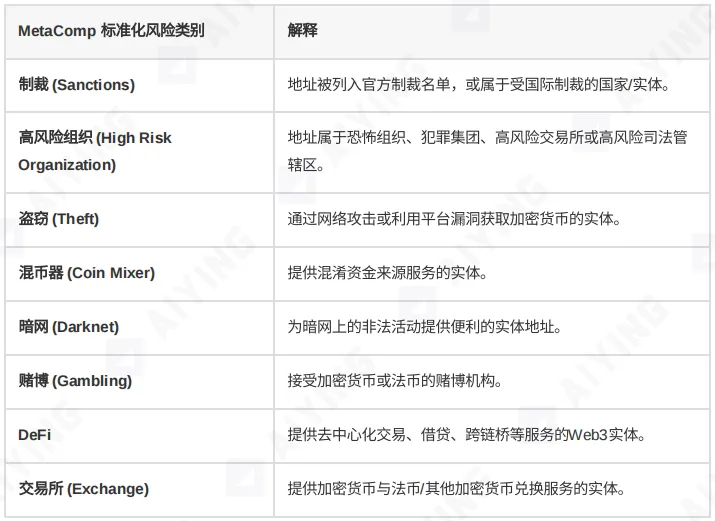
This enables new tools to be quickly “translated” for cross-platform decisions.
Step 2: Unify Risk Thresholds—Draw Clear Lines
Once you have a common language, codify your risk appetite and compliance requirements into specific, trackable thresholds—not just dollar amounts, but nuanced, multidimensional parameters:
- Severity levels: Define “severe” (sanctions, terror finance), “high risk” (theft, darknet), “acceptable” (exchanges, DeFi), and so on.
- Transaction-level taint %: Set data-driven triggers for what proportion of a transaction’s value comes from high-risk sources.
- Wallet-level cumulative taint %: Define long-term risk exposure for wallets with repeated gray-market activity.
These red lines make the compliance process clear, consistent, and legally defensible.
Step 3: Multi-Layer Screening—From Single Events to Patterns
Now connect these standards and thresholds in a multi-layered, automated workflow—a precise funnel that filters risk at every level without bogging down routine business.
Key workflow steps include:
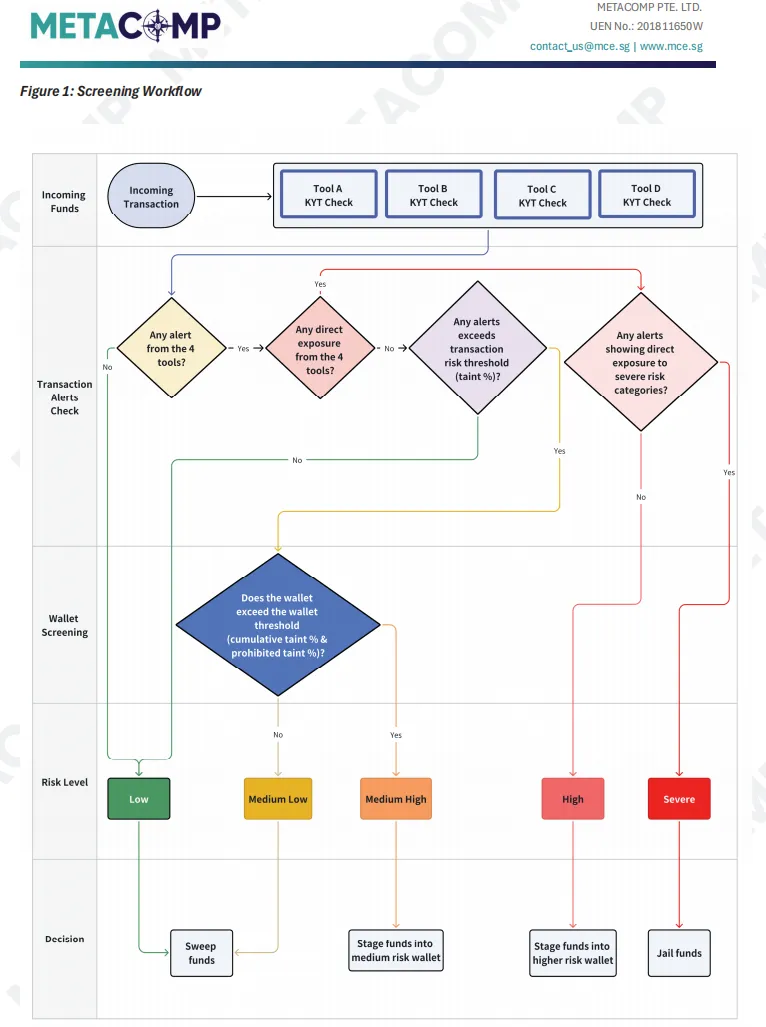
Figure 4: Example Multi-Layer Screening Workflow (from MetaComp KYT Methodology)
- Initial screening—run all transactions and counterparties through your trio of tools. Any alert moves the transaction forward.
- Direct exposure assessment—if a counterparty is already flagged “severe” or “high risk,” immediate freeze or manual review is triggered.
- Transaction-level analysis—if not, trace the funds; if a sufficient proportion comes from risk sources, move forward.
- Wallet-level analysis—check the wallet’s long-term risk; if it’s above threshold, flag the transaction as high risk.
- Final decision—route the outcome (clear, block, refund, report) based on the risk rating, automatically or with human input.
This approach transforms risk detection from a simple yes/no to a pattern-based, multi-dimensional process—allocating resources to high-risk cases and clearing low-risk ones quickly, effectively balancing risk and user experience.
Conclusion: Tear Down the Stage—Return to the Battlefield
This deep dive into zombie systems and “Compliance Theater” makes one thing clear: the real danger is not wasted money, but a false sense of security. It blinds leadership, numbs staff, and leaves organizations dangerously exposed.
In an era where financial crime evolves as fast as financial innovation, relying on a single KYT tool is like running naked across a battlefield. Criminals have automated scripts, cross-chain bridges, privacy coins, DeFi mixers—a threat landscape more complex than ever. If your defenses are stuck in the past, it’s not if you’ll get breached, but when.
True compliance is not a show, but a battle. It needs layered tools, rigorous strategy, and skilled professionals—no flash, no applause, just respect for risk, honest data, and relentless process improvement.
To every industry professional—especially those with the power to shape policy: abandon dreams of a “silver bullet.” There is no tool that solves every compliance challenge forever. You must continually evolve your defenses, learn from live data, and adapt daily. The systems you build today may have loopholes tomorrow; vigilance, learning, and adaptation are your only options.
It’s time to tear down the “Compliance Theater” and bring true, battle-ready compliance systems to the front lines. Only then can we protect the value we strive to create.
Disclaimer:
- This article is reposted from [Aiying Payment Compliance], with copyright belonging to the original author [Aiying AML Peter]. If there are concerns about this repost, please contact the Gate Learn team, who will promptly handle the matter as appropriate.
- Disclaimer: The views and opinions expressed are solely those of the author and do not constitute investment advice.
- Other language versions are translated by the Gate Learn team; reproduction, distribution, or plagiarism of these translations without explicit reference to Gate is prohibited.
Related Articles

Solana Need L2s And Appchains?

The Future of Cross-Chain Bridges: Full-Chain Interoperability Becomes Inevitable, Liquidity Bridges Will Decline

Sui: How are users leveraging its speed, security, & scalability?

Navigating the Zero Knowledge Landscape

What Is Ethereum 2.0? Understanding The Merge
